
Every day we are surrounded by more and more different devices that support the Internet. Each of us at least owns a smartphone with which you can access the Internet, plus everything else we have a couple of devices that also have access to the world wide web if necessary. It is difficult to imagine, but at the moment there are more than 3.5 billion Internet users and this is not the limit. Moreover, in the near future it is expected an incredible jump in the number of devices that have access to the Internet, this includes smartphones and tablets, and laptops, and TVs, and other objects with IOT sensors. Many researchers claim that by 2025 their total number could reach 75 billion units. Thus, we can conclude that in the near future our daily life will be directly connected to the Internet.
Problems
However, with the advent of such a huge number of objects with access to the Internet, makes us and our lives vulnerable, and most importantly exposes unnecessary danger. What danger am I talking about? It's really very obvious. We all know that with the help of the Internet and open access to the Internet, many hackers have the opportunity to hack into our databases, use some confidential information or even worse to implant us a different virus, which as a result can ruin our device.
At the same time, many of us do not even suspect that there are various resources on the Internet that monitor us day and night, where we are, and what we are, what social networks we have in priority, what we are interested in, what sites we visit, from what device, how much, and almost from what IP address. All these data are collected without our knowledge or consent.
Another pressing problem of the Internet is hype, which just climbs from where she is not lazy and often turns from a non-Intrusive ads in the usual spam. This and many other things makes you think, and what will happen next if you can not control it?
It is good that the world is moving a little faster and the bright minds of mankind have long been developed to solve this problem. This is the decision we will discuss with you today.
About the project
The project is called – HONEYPOD. Its main task is to provide a secure connection of our devices to the Internet.
The versatility of this project is that the Honeypod is a small device that connects to our home router and controls the entire flow of information through itself, while filtering out malicious applications, various kinds of virus data, spam advertising and other nonsense that can adversely affect the operation of our devices. Thus Honeypod not only safely monitors all connections to the network, but also accelerates the processes of communication, increasing the data transfer speed at least twice.
Design feature
The main feature of the Honeypod is that it is a convenient and portable smart unit that is no bigger than the size of your palm, making it convenient to use and compact indoors. At the same time, the Honeypodcannot be detected, hacked or blocked from the outside, which makes it even more reliable and efficient to use. However, the developers claim that Honeypod is more like a pass-through authenticator device, which not only checks, but also protects your mobile device from various tracking systems, advertising spam and connection of some third parties.
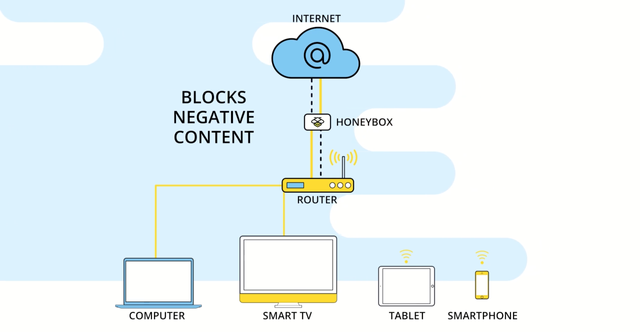
To ensure maximum security, Honeypod uses modern blockchain technology, which helps to solve various nuances of the device operation at all stages of its network verification. It works simply elementary, for clarity, I propose to look at the following illustration, where a simple example shows the operation of the system Honeypod.

Advantages
The advantages of the Honeypod quite a lot and the most important of them are that:
- Honeypod blocks malicious data at once, without sending it to you directly, and then exposing them to blocking;
- Honeypod does not require any additional software installation on all your mobile devices with Internet access. Honeypod has only its own unit, with which all the necessary filtering takes place;
- Honeypod protects absolutely all devices that have access to the Internet, regardless of whether any browser is installed in them;
- all processes in the Honeypod user has the ability to control yourself, expressing a desire to adjust the standard list of filtering unwanted systems and more.
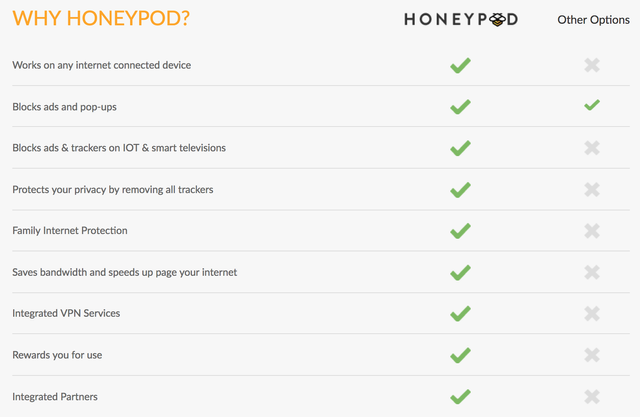
The details of the ICO
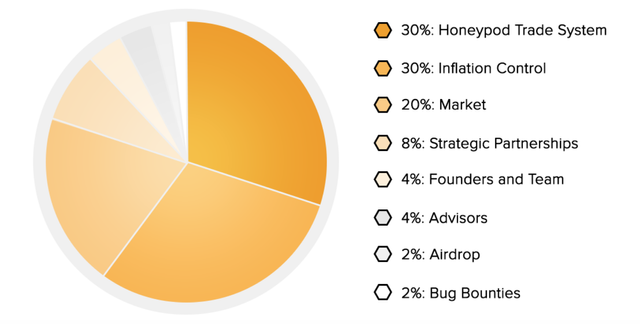
Since the project is a decentralized network through which malware, websites and other third parties will be blocked, you can use their personal cryptocurrency – HNY, which will soon be available for purchase, to buy and purchase the Honeypod block. The total day of sale will be allocated 1 billion coins, the initial cost of which is $0.05 per 1 HNY. At the same time, several stages of sales will be allocated, where the cost of coins will be significantly lower due to the offered discounts and various promotions. The end date of sales is unknown, as sales will end immediately after they collect a Hard Cap of $ 10 million.
The distribution of tokens is as follows:
Conclusion
Given the rapid growth of the Internet of things and devices that support access to the world wide web, it is absolutely obvious that our security will hang on a thin thread if we do not take any measures. Honeypod perfectly demonstrated its feature and advantages, thanks to which it becomes obvious that this kind of device we all need, because it is able to protect us from all kinds of problems associated with the Internet.
I dare to assume that the idea of the Honeypod will appeal to many, because I do not think that there are people in the world who are indifferent to their safety and security of their mobile devices. Therefore, the project has all chances to take a leading position in this segment.
If you want to know more information about the Honeypod, I offer you all the official resources of the project, the links that I attached at the end of the review.

INFORMATION:
 TELEGRAM: https://t.me/honeypod
TELEGRAM: https://t.me/honeypod
Tidak ada komentar:
Posting Komentar